Microsoft is publishing a relatively light 54 new vulnerabilities this December 2025 Patch Tuesday, which is significantly lower than we have come to expect over the past couple of years. Today’s list includes two publicly disclosed remote code vulnerabilities, and a single exploited-in-the-wild vulnerability. Three critical remote code execution (RCE) vulnerabilities are also patched today; Microsoft currently assesses those as less likely or even unlikely to see exploitation. During December, Microsoft has already patched 14 browser vulnerabilities and more than 80 vulnerabilities in open source products, which are not included in the Patch Tuesday count above.
Windows Cloud Files minifilter: zero-day EoP
Microsoft has evidence that attackers are already making full use of CVE-2025-62221, a zero-day local elevation of privilege (EoP) vulnerability in the Windows Cloud Files Mini Filter Driver leading to SYSTEM privileges. File system filter drivers, aka minifilters, attach to the system software stack, and intercept requests targeted at a file system, and extend or replace the functionality provided by the original target. Typical use cases include data encryption, automated backup, on-the-fly compression, and cloud storage.
The Cloud Files minifilter is used by OneDrive, Google Drive, iCloud, and others, although as a core Windows component, it would still be present on a system where none of those apps were installed. Microsoft ranks CVE-2025-62221 as important rather than critical, since an attacker would need to have an existing foothold on the target system, but since it’s already exploited in the wild and leads to SYSTEM privileges, all but the most optimistic blue team threat models will surely treat CVE-2025-62221 as a top priority for remediation.
PowerShell: zero-day RCE
Under normal circumstances, PowerShell does a decent job of looking out for the unwary end user, and will wait for confirmation or even outright block unexpected attempts to run code from the internet that isn’t signed by a trusted publisher. Windows Mark-of-the-Web (MotW) functionality tracks files that were downloaded from the internet, but CVE-2025-54100 is a zero-day vulnerability which allows attackers to sidestep security controls that rely on MotW by the simple expedient of relying on code execution before the file is ever written. Microsoft is aware of public disclosure.
The Windows security updates published today address CVE-2025-54100 by altering the default functionality of Invoke-WebRequest in PowerShell 5.1 so that it will prompt the user, instead of simply executing potentially malicious code as it processes the full Document Object Model of the requested remote resource. Scripts that rely on the impacted functionality may hang indefinitely when encountering the new prompt, unless updated to pass the -UseBasicParsing parameter to Invoke-WebRequest, since this explicitly avoids the potential for script execution. PowerShell 7 avoids all of this by moving beyond dependency on the legacy MSHTML/Trident engine, which used to power Internet Explorer. However, PowerShell 5.1 is what’s installed by default with a fresh Windows installation, even for Server 2025 and Windows 11 25H2, because Microsoft has a hard time telling enterprise customers that continuing support for legacy business applications comes with an ever-increasing security cost.
Copilot: zero-day
The GitHub Copilot for Jetbrains plugin promises users that they can take control of their code using Copilot Edit Mode. Unfortunately, an attacker exploiting CVE-2025-64671 will be aiming to do something very similar. Microsoft is aware of public disclosure. In this scenario, cross-prompt injection, where an attacker hides malicious instructions inside a malicious file or within MCP server data, can lead to arbitrary command execution, where unsafe commands sneak past security boundaries while appended to safe, allowlisted commands. This issue is by no means specific to Copilot or Jetbrains; as the original researcher points out, this is an example of an entire class of vulnerabilities, where the addition of agentic AI to an IDE extends and alters the attack surface. Other well-known IDE vendors have assigned CVEs and/or published patches for broadly similar issues.
Office: two critical no-click RCEs
Microsoft Office is widely deployed, and it’s a rare Patch Tuesday when it doesn’t receive at least a few security updates. Two Office RCEs are particularly noteworthy this month. The advisory FAQs for both CVE-2025-62554 and CVE-2025-62557 mention that the Preview Pane is a vector, so a user who scrolls past a malicious email in Outlook or a sketchy file in Explorer could trigger exploitation without doing anything obviously wrong. However, it gets worse, because even receiving a specially-crafted email could trigger exploitation, without any requirement that the user open, read, or click on the malicious link within it. CVE-2023-23397, a widely-discussed critical Outlook vulnerability from some two-and-a-half years ago shares these characteristics. In that case, Microsoft detected in-the-wild exploitation by a Russia-based threat actor targeting government, military, and critical infrastructure targets in Europe. While there’s no suggestion that either of the vulnerabilities patched today necessarily result in NTLM hash disclosure in the same vein as CVE-2023-23397, the potential for exploitation without the need for any user interaction is a serious concern.
Microsoft lifecycle update
There are no significant Microsoft product lifecycle changes this month. Visual Studio 2022 LTSC 17.10 will reach end of life in January.
Summary charts
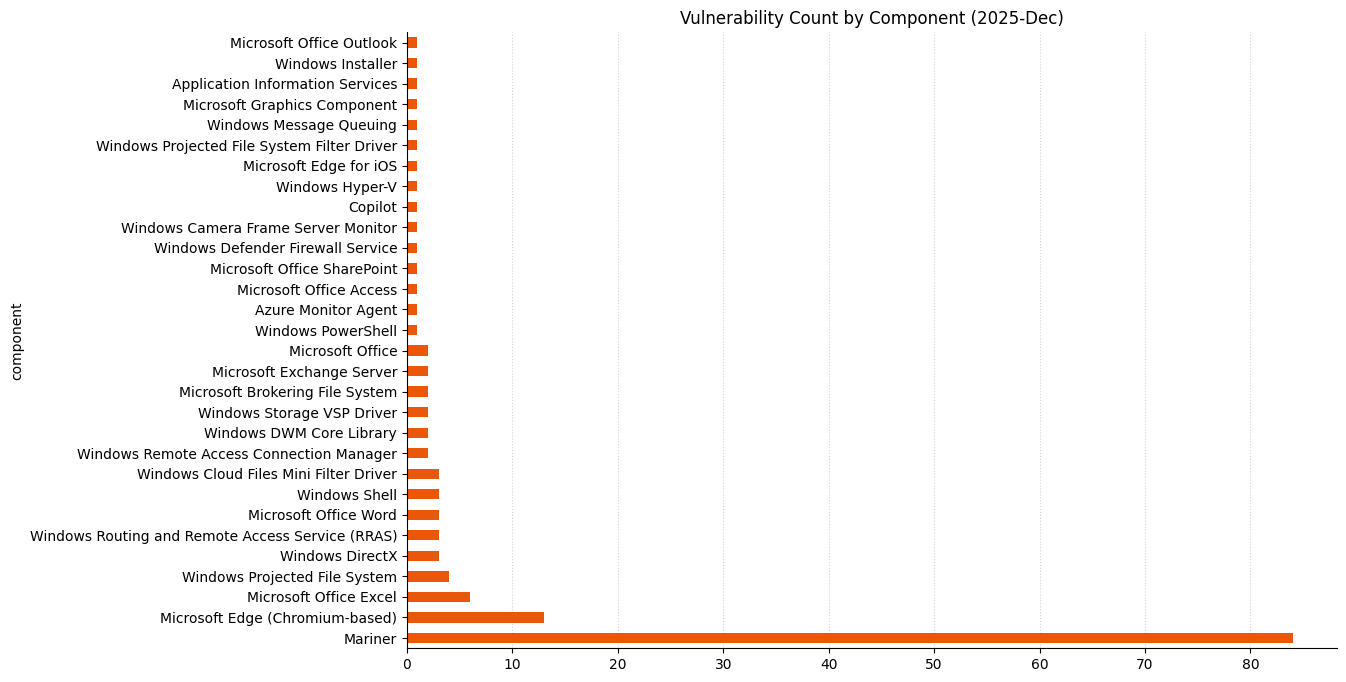
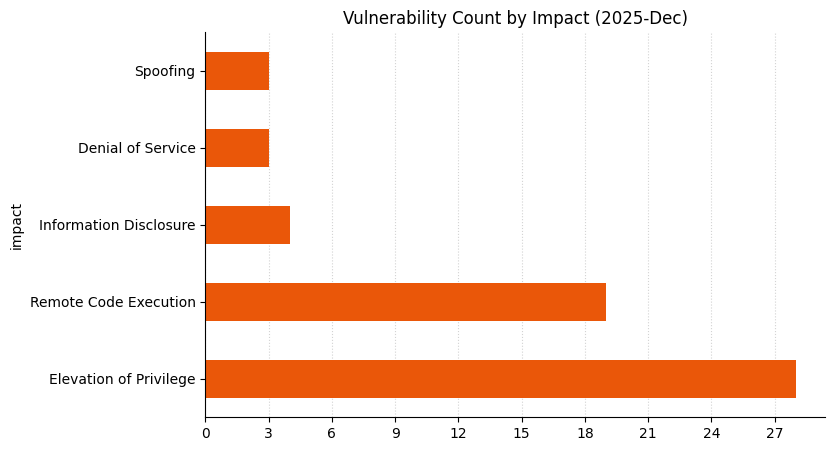
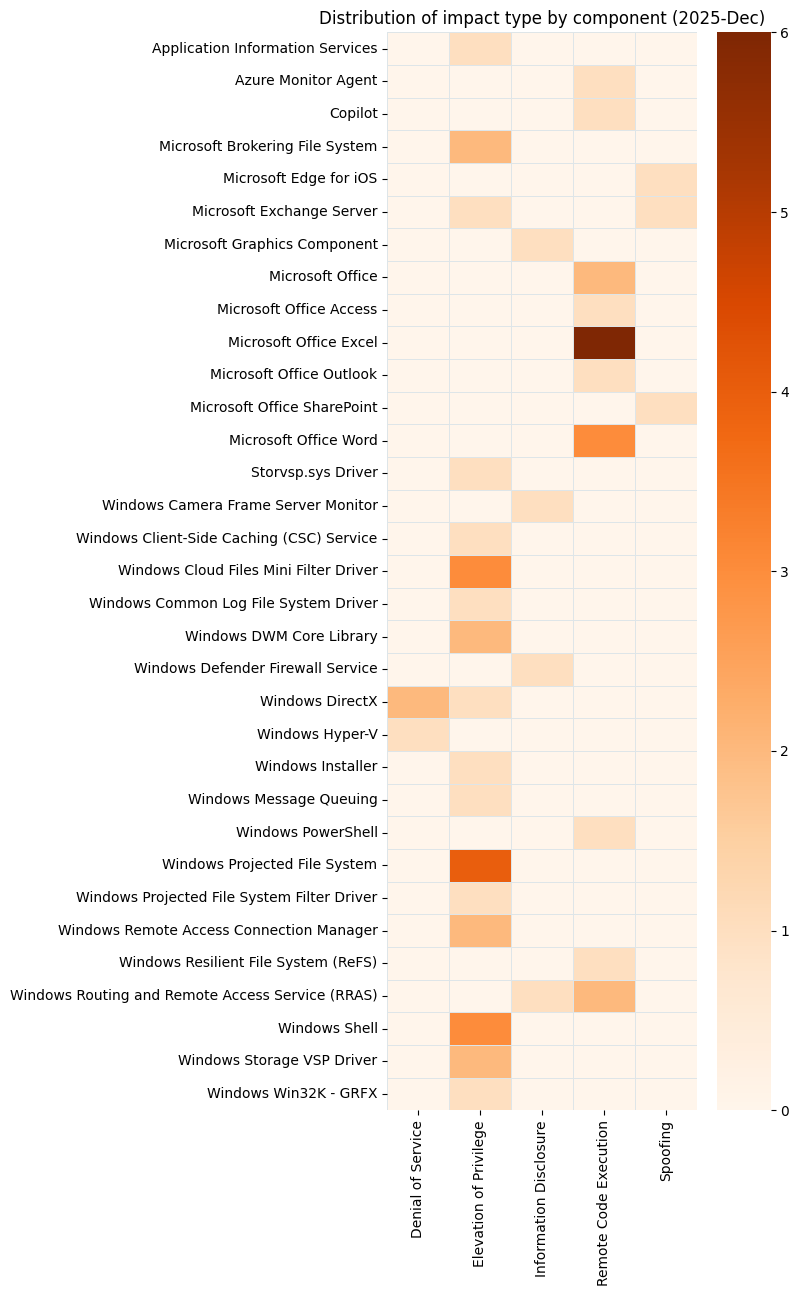
Summary tables
Azure vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Azure Monitor Agent Remote Code Execution Vulnerability
No
No
8.8
Browser vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Microsoft Edge (Chromium-based) for Mac Spoofing Vulnerability
No
No
4.3
Chromium: CVE-2025-13721 Race in v8
No
No
N/A
Chromium: CVE-2025-13720 Bad cast in Loader
No
No
N/A
Chromium: CVE-2025-13640 Inappropriate implementation in Passwords
No
No
N/A
Chromium: CVE-2025-13639 Inappropriate implementation in WebRTC
No
No
N/A
Chromium: CVE-2025-13638 Use after free in Media Stream
No
No
N/A
Chromium: CVE-2025-13637 Inappropriate implementation in Downloads
No
No
N/A
Chromium: CVE-2025-13636 Inappropriate implementation in Split View
No
No
N/A
Chromium: CVE-2025-13635 Inappropriate implementation in Downloads
No
No
N/A
Chromium: CVE-2025-13634 Inappropriate implementation in Downloads
No
No
N/A
Chromium: CVE-2025-13633 Use after free in Digital Credentials
No
No
N/A
Chromium: CVE-2025-13632 Inappropriate implementation in DevTools
No
No
N/A
Chromium: CVE-2025-13631 Inappropriate implementation in Google Updater
No
No
N/A
Chromium: CVE-2025-13630 Type Confusion in V8
No
No
N/A
Mariner vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Untrusted search path in auth_query connection in PgBouncer
No
No
7.5
Apache HTTP Server: NTLM Leakage on Windows through UNC SSRF
No
No
7.5
Apache HTTP Server: CGI environment variable override
No
No
6.5
Apache HTTP Server: mod_userdir+suexec bypass via AllowOverride FileInfo
No
No
5.4
Microsoft Office vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Microsoft SharePoint Server Spoofing Vulnerability
No
No
8.8
Microsoft Office Remote Code Execution Vulnerability
No
No
8.4
Microsoft Office Remote Code Execution Vulnerability
No
No
8.4
Microsoft Word Remote Code Execution Vulnerability
No
No
7.8
Microsoft Word Remote Code Execution Vulnerability
No
No
7.8
Microsoft Outlook Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Excel Remote Code Execution Vulnerability
No
No
7.8
Microsoft Access Remote Code Execution Vulnerability
No
No
7.8
Microsoft Word Remote Code Execution Vulnerability
No
No
7
Open Source Software vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
hfsplus: fix KMSAN uninit-value issue in __hfsplus_ext_cache_extent()
No
No
9.8
gfs2: Fix unlikely race in gdlm_put_lock
No
No
9.8
devlink: rate: Unset parent pointer in devl_rate_nodes_destroy
No
No
9.8
Input: imx_sc_key - fix memory corruption on unload
No
No
9.8
sctp: avoid NULL dereference when chunk data buffer is missing
No
No
8.6
usb: cdns3: gadget: Use-after-free during failed initialization and exit of cdnsp gadget
No
No
7.8
most: usb: Fix use-after-free in hdm_disconnect
No
No
7.8
mm/secretmem: fix use-after-free race in fault handler
No
No
7.8
bpf: Sync pending IRQ work before freeing ring buffer
No
No
7.8
Vim for Windows Uncontrolled Search Path Element Remote Code Execution Vulnerability
No
No
7.8
drm/vmwgfx: Validate command header size against SVGA_CMD_MAX_DATASIZE
No
No
7.3
x86: fix clear_user_rep_good() exception handling annotation
No
No
7.1
ocfs2: clear extent cache after moving/defragmenting extents
No
No
7.1
jfs: Verify inode mode when loading from disk
No
No
7.1
fbdev: bitblit: bound-check glyph index in bit_putcs*
No
No
7.1
KVM: arm64: Check the untrusted offset in FF-A memory share
No
No
7.1
Bluetooth: hci_event: validate skb length for unknown CC opcode
No
No
7.1
Bluetooth: btusb: reorder cleanup in btusb_disconnect to avoid UAF
No
No
7.1
virtio-net: fix received length check in big packets
No
No
7
tipc: Fix use-after-free in tipc_mon_reinit_self().
No
No
7
sctp: prevent possible shift-out-of-bounds in sctp_transport_update_rto
No
No
7
net: bridge: fix use-after-free due to MST port state bypass
No
No
7
mptcp: fix race condition in mptcp_schedule_work()
No
No
7
NFSD: free copynotify stateid in nfs4_free_ol_stateid()
No
No
7
9p/trans_fd: p9_fd_request: kick rx thread if EPOLLIN
No
No
7
nvme: nvme-fc: Ensure ->ioerr_work is cancelled in nvme_fc_delete_ctrl()
No
No
6.6
hfs: fix KMSAN uninit-value issue in hfs_find_set_zero_bits()
No
No
6.6
wifi: brcmfmac: fix crash while sending Action Frames in standalone AP Mode
No
No
6.5
vsock: Ignore signal/timeout on connect() if already established
No
No
6.3
mptcp: fix a race in mptcp_pm_del_add_timer()
No
No
6.3
scsi: sg: Do not sleep in atomic context
No
No
6.2
net: qlogic/qede: fix potential out-of-bounds read in qede_tpa_cont() and qede_tpa_end()
No
No
6.1
xfrm: delete x->tunnel as we delete x
No
No
5.5
usb: gadget: f_fs: Fix epfile null pointer access after ep enable.
No
No
5.5
smb/server: fix possible refcount leak in smb2_sess_setup()
No
No
5.5
smb/server: fix possible memory leak in smb2_read()
No
No
5.5
s390/ctcm: Fix double-kfree
No
No
5.5
regmap: slimbus: fix bus_context pointer in regmap init calls
No
No
5.5
pidfs: validate extensible ioctls
No
No
5.5
orangefs: fix xattr related buffer overflow...
No
No
5.5
ntfs3: pretend $Extend records as regular files
No
No
5.5
nios2: ensure that memblock.current_limit is set when setting pfn limits
No
No
5.5
net: sched: act_ife: initialize struct tc_ife to fix KMSAN kernel-infoleak
No
No
5.5
net: sched: act_connmark: initialize struct tc_ife to fix kernel leak
No
No
5.5
net: openvswitch: remove never-working support for setting nsh fields
No
No
5.5
net/mlx5: Clean up only new IRQ glue on request_irq() failure
No
No
5.5
iommufd: Don't overflow during division for dirty tracking
No
No
5.5
fuse: fix livelock in synchronous file put from fuseblk workers
No
No
5.5
fbdev: Add bounds checking in bit_putcs to fix vmalloc-out-of-bounds
No
No
5.5
fbcon: Set fb_display[i]->mode to NULL when the mode is released
No
No
5.5
exfat: validate cluster allocation bits of the allocation bitmap
No
No
5.5
exfat: fix improper check of dentry.stream.valid_size
No
No
5.5
drm/msm: Fix pgtable prealloc error path
No
No
5.5
drm/amdgpu: hide VRAM sysfs attributes on GPUs without VRAM
No
No
5.5
cifs: client: fix memory leak in smb3_fs_context_parse_param
No
No
5.5
btrfs: ensure no dirty metadata is written back for an fs with errors
No
No
5.5
be2net: pass wrb_params in case of OS2BMC
No
No
5.5
amd/amdkfd: resolve a race in amdgpu_amdkfd_device_fini_sw
No
No
5.5
accel/habanalabs: support mapping cb with vmalloc-backed coherent memory
No
No
5.5
PCI/IOV: Add PCI rescan-remove locking when enabling/disabling SR-IOV
No
No
5.5
NFSD: Fix crash in nfsd4_read_release()
No
No
5.5
Input: cros_ec_keyb - fix an invalid memory access
No
No
5.5
Bluetooth: bcsp: receive data only if registered
No
No
5.5
Bluetooth: SCO: Fix UAF on sco_conn_free
No
No
5.5
Bluetooth: MGMT: cancel mesh send timer when hdev removed
No
No
5.5
Bluetooth: MGMT: Fix OOB access in parse_adv_monitor_pattern()
No
No
5.5
Bluetooth: 6lowpan: reset link-local header on ipv6 recv path
No
No
5.5
ALSA: usb-audio: Fix NULL pointer dereference in snd_usb_mixer_controls_badd
No
No
5.5
drm/amdgpu: Fix NULL pointer dereference in VRAM logic for APU devices
No
No
4.7
ALSA: usb-audio: Fix potential overflow of PCM transfer buffer
No
No
4.3
mm/damon/vaddr: do not repeat pte_offset_map_lock() until success
No
No
4.1
Improper validation of tag size in Text component parser
No
No
N/A
Open Source Software Mariner vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Excessive resource consumption when printing error string for host certificate validation in crypto/x509
No
No
7.5
LIBPNG has an out-of-bounds read in png_image_read_composite
No
No
7.1
Improper application of excluded DNS name constraints when verifying wildcard names in crypto/x509
No
No
6.5
A denial-of-service vulnerability exists in github.com/sirupsen/logrus when using Entry.Writer() to log a single-line payload larger than 64KB without newline characters.
No
No
5.9
Quadratic complexity in node ID cache clearing
No
No
N/A
Out-of-memory when loading Plist
No
No
N/A
KissFFT Integer Overflow Heap Buffer Overflow via kiss_fft_alloc
No
No
N/A
Excessive read buffering DoS in http.client
No
No
N/A
Other vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
GitHub Copilot for Jetbrains Remote Code Execution Vulnerability
No
Yes
8.4
Server Software ESU vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Microsoft Exchange Server Elevation of Privilege Vulnerability
No
No
7.5
Microsoft Exchange Server Spoofing Vulnerability
No
No
5.3
Windows vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Windows Resilient File System (ReFS) Remote Code Execution Vulnerability
No
No
8.8
Windows Storage VSP Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Storage VSP Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Storage VSP Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Shell Elevation of Privilege Vulnerability
No
No
7.8
Windows Projected File System Elevation of Privilege Vulnerability
No
No
7.8
Windows Projected File System Elevation of Privilege Vulnerability
No
No
7.8
Windows Projected File System Elevation of Privilege Vulnerability
No
No
7.8
Windows Projected File System Elevation of Privilege Vulnerability
No
No
7.8
Windows Projected File System Elevation of Privilege Vulnerability
No
No
7.8
Windows DWM Core Library Elevation of Privilege Vulnerability
No
No
7.8
Windows DWM Core Library Elevation of Privilege Vulnerability
No
No
7.8
Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Yes
No
7.8
Application Information Service Elevation of Privilege Vulnerability
No
No
7.8
Windows File Explorer Elevation of Privilege Vulnerability
No
No
7.5
Windows File Explorer Elevation of Privilege Vulnerability
No
No
7.3
Windows Camera Frame Server Monitor Information Disclosure Vulnerability
No
No
7.1
Microsoft Brokering File System Elevation of Privilege Vulnerability
No
No
7
Microsoft Brokering File System Elevation of Privilege Vulnerability
No
No
7
DirectX Graphics Kernel Elevation of Privilege Vulnerability
No
No
7
Windows DirectX Information Disclosure Vulnerability
No
No
6.5
DirectX Graphics Kernel Denial of Service Vulnerability
No
No
6.5
DirectX Graphics Kernel Denial of Service Vulnerability
No
No
6.5
Windows Defender Firewall Service Information Disclosure Vulnerability
No
No
4.4
Windows ESU vulnerabilities
CVE
Title
Exploited?
Publicly disclosed?
CVSSv3 base score
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
No
No
8.8
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
No
No
8.8
Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
No
No
7.8
Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
No
No
7.8
Windows Installer Elevation of Privilege Vulnerability
No
No
7.8
Windows Common Log File System Driver Elevation of Privilege Vulnerability
No
No
7.8
Windows Client-Side Caching Elevation of Privilege Vulnerability
No
No
7.8
Win32k Elevation of Privilege Vulnerability
No
No
7.8
PowerShell Remote Code Execution Vulnerability
No
Yes
7.8
Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability
No
No
7.8
Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability
No
No
6.5
Windows Hyper-V Denial of Service Vulnerability
No
No
5.3
- Patch Tuesday
- Vulnerability Management