Microsoft is publishing 114 vulnerabilities this January 2026 Patch Tuesday. Today’s menu includes just one vulnerability marked as exploited in the wild, as well as two vulnerabilities where Microsoft is aware of public disclosure. There are no critical remote code execution or elevation of privilege vulnerabilities. So far this month, Microsoft has already provided patches to address one browser vulnerability and around a dozen vulnerabilities in open source products, which are not included in the Patch Tuesday count above.
Windows DWM: exploited-in-the-wild information disclosure
The Windows Desktop Windows Manager (DWM) is a high value target for vulnerability researchers and threat actors, and CVE-2026-20805 is the latest in an occasional series of exploited-in-the-wild zero-day vulnerabilities to have emerged from it. DWM is responsible for drawing everything on the display of a Windows system, which means it offers an enticing combination of privileged access and universal availability, since just about any process might need to display something. In this case, exploitation leads to improper disclosure of an ALPC port section address, which is a section of user mode memory where Windows components coordinate various actions between themselves.
The CVSS v3 score of 5.5 evaluates to medium severity, which wouldn’t typically scream “patch me first”, but Microsoft evaluates CVE-2026-20805 as important on their proprietary severity scale, and information disclosure vulnerabilities by their very nature tend to end up with lower CVSS scores, since there’s no direct impact on integrity or availability. Also, Microsoft information disclosure vulnerabilities very rarely end up marked as exploited in the wild; any that do are very likely to be part of a longer exploit chain. In this case, it’s likely that the improperly disclosed memory address gives an attacker a starting point in the hunt for the in-memory address of the DWM process, sidestepping Address Space Layout Randomization (ASLR), and greatly increasing the chance of developing a stable elevation of privilege exploit for DWM rather than a flakey blue screen of death generator.
Windows Agere modem driver: publicly disclosed elevation of privilege
Back in October 2025, Microsoft removed a specific modem driver ltmdm64.sys from all versions of Windows, after it was implicated in CVE-2025-24052, an exploited-in-the-wild elevation of privilege vulnerability. Today sees another couple of modem drivers removed from Windows for a broadly similar reason: Microsoft is aware of functional exploit code for an elevation of privilege vulnerability in a very similar modem driver, tracked as CVE-2023-31096. That’s not a typo; this vulnerability was originally published via MITRE over two years ago, along with a credible public writeup by the original researcher. Today’s Windows patches remove agrsm64.sys and agrsm.sys. All three modem drivers were originally developed by the same now-defunct third party, and have been included in Windows for decades. These driver removals will pass unnoticed for most people, but you might find active modems still in a few contexts, including some industrial control systems.
Two questions remain: how many more legacy modem drivers are still present on a fully-patched Windows asset, and how many more elevation-to-SYSTEM vulnerabilities will emerge from them before Microsoft cuts off attackers who have been enjoying living off the land[line] by exploiting an entire class of dusty old device drivers? Although Microsoft doesn’t claim evidence of exploitation for CVE-2023-31096, the relevant 2023 write-up and the 2025 removal of the other Agere modem driver have provided two strong signals for anyone looking for Windows exploits in the meantime. In case you were wondering, there is no need to have a modem connected; the mere presence of the driver is enough to render an asset vulnerable.
Secure Boot: critical security feature bypass
Today sees the publication of CVE-2026-21265, which is a critical security feature bypass vulnerability affecting Windows Secure Boot. Fifteen years is a very long time indeed in information security, but the clock is running out on the Microsoft root certificates which have been signing essentially everything in the Secure Boot ecosystem since the days of Stuxnet. Microsoft issued replacement certificates back in 2023, alongside CVE-2023-24932 which covered relevant Windows patches as well as subsequent steps to remediate the Secure Boot bypass exploited by the BlackLotus bootkit.
Once the ancient 2011 certificates expire later this year, Windows devices that do not have the new 2023 certificates can no longer receive Secure Boot security fixes. When updating the bootloader and BIOS, it is essential to prepare fully ahead of time for the specific OS and BIOS combination you’re working with, since incorrect remediation steps can lead to an unbootable system.
Microsoft lifecycle update
Visual Studio 2022 LTSC 17.10 reaches end of support today, so now is a good time to upgrade to a newer minor version. Dynamics CRM 2016 (also known as Dynamics 365) also reaches end of life. There are no other significant Microsoft product lifecycle changes this month.
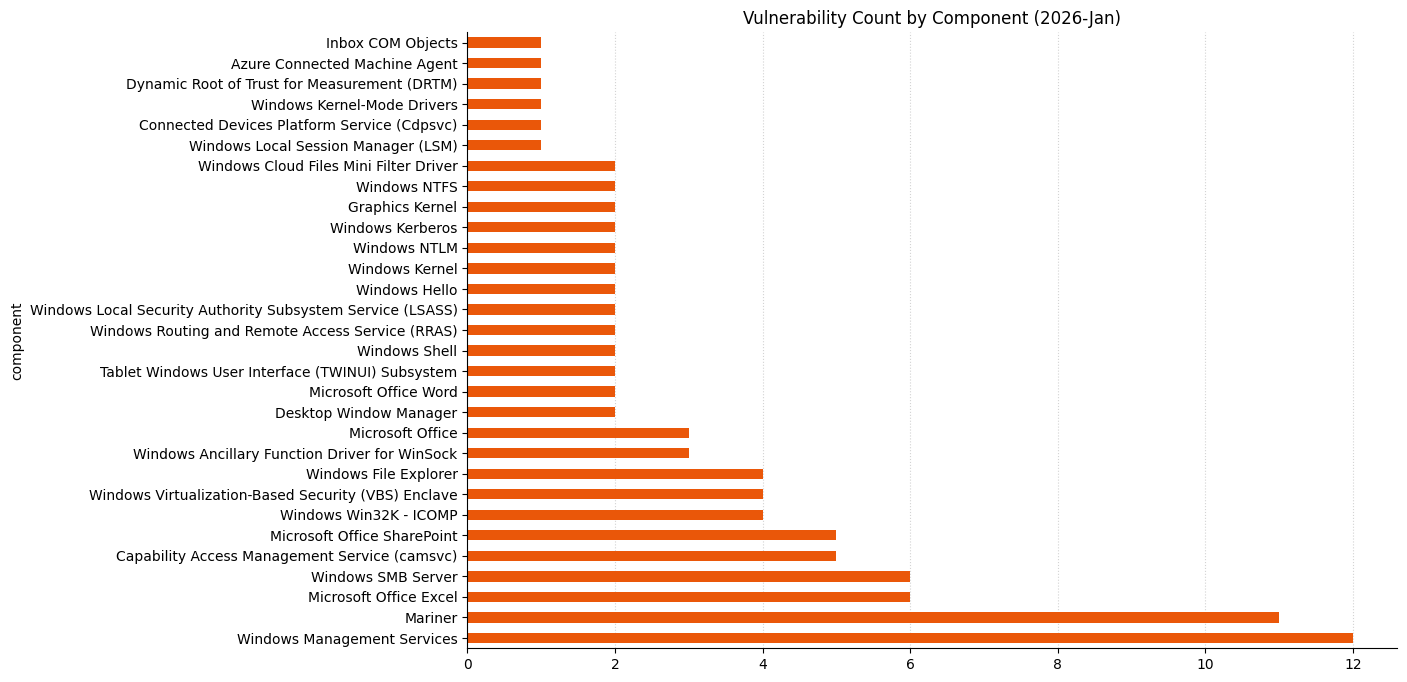
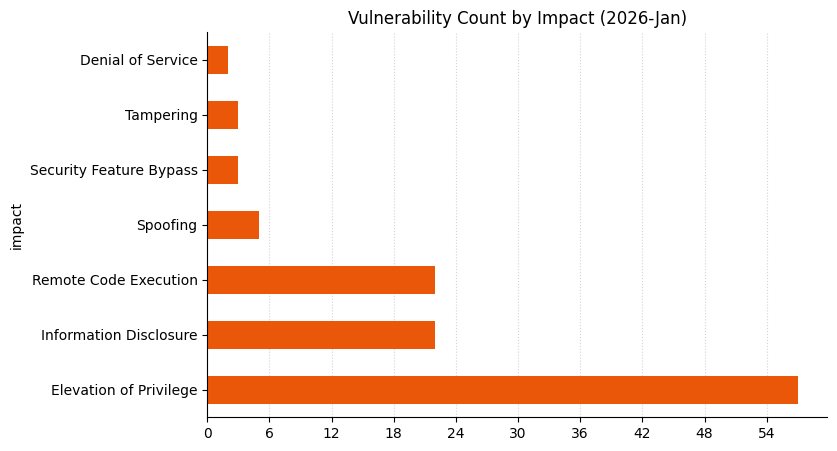
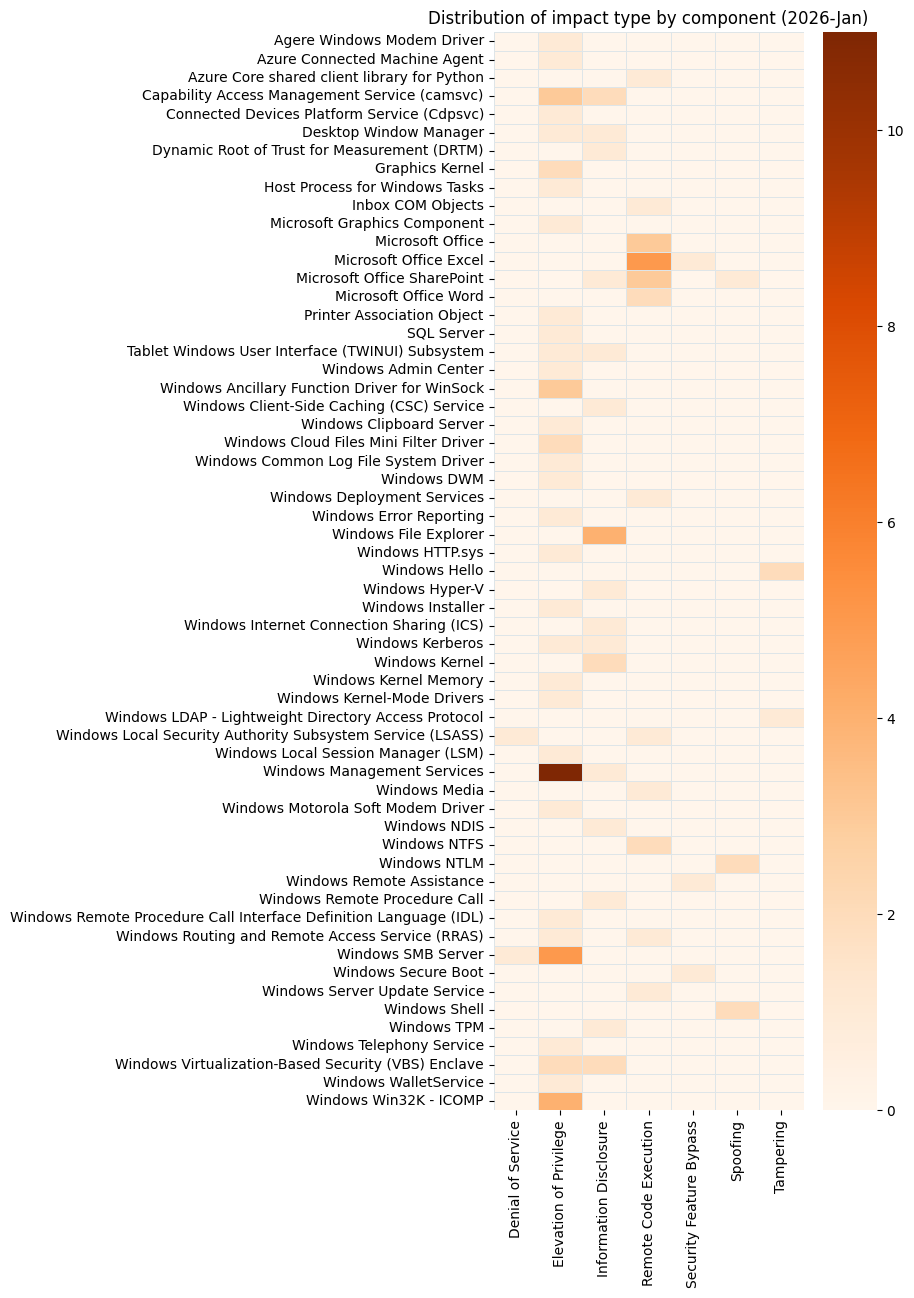
Vulnerabilities by Product Family
Azure vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-21224Azure Connected Machine Agent Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-21226Azure Core shared client library for Python Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.5
CVE-2026-20965Windows Admin Center Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.5
Developer Tools vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-21219Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability
Exploitation Unlikely
No
7.0
ESU vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-20805Desktop Window Manager Information Disclosure Vulnerability
Exploitation Detected
No
5.5
CVE-2026-20847Microsoft Windows File Explorer Spoofing Vulnerability
Exploitation Unlikely
No
6.5
CVE-2023-31096MITRE: CVE-2023-31096 Windows Agere Soft Modem Driver Elevation of Privilege Vulnerability
Exploitation More Likely
Yes
7.8
CVE-2026-20925NTLM Hash Disclosure Spoofing Vulnerability
Exploitation Less Likely
No
6.5
CVE-2026-20872NTLM Hash Disclosure Spoofing Vulnerability
Exploitation Less Likely
No
6.5
CVE-2026-20821Remote Procedure Call Information Disclosure Vulnerability
Exploitation Unlikely
No
6.2
CVE-2026-21265Secure Boot Certificate Expiration Security Feature Bypass Vulnerability
Exploitation Less Likely
Yes
6.4
CVE-2026-20831Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20860Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20839Windows Client-Side Caching (CSC) Service Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20940Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20820Windows Common Log File System Driver Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-0386Windows Deployment Services Remote Code Execution Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20929Windows HTTP.sys Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20816Windows Installer Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20849Windows Kerberos Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20833Windows Kerberos Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20809Windows Kernel Memory Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20875Windows Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability
Exploitation Less Likely
No
7.5
CVE-2026-20869Windows Local Session Manager (LSM) Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2024-55414Windows Motorola Soft Modem Driver Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20936Windows NDIS Information Disclosure Vulnerability
Exploitation Unlikely
No
4.3
CVE-2026-20840Windows NTFS Remote Code Execution Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20922Windows NTFS Remote Code Execution Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20824Windows Remote Assistance Security Feature Bypass Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20828Windows rndismp6.sys Information Disclosure Vulnerability
Exploitation Less Likely
No
4.6
CVE-2026-20843Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20868Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.8
CVE-2026-20856Windows Server Update Service (WSUS) Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.1
CVE-2026-20927Windows SMB Server Denial of Service Vulnerability
Exploitation Unlikely
No
5.3
CVE-2026-20919Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20921Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20926Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20934Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20848Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20834Windows Spoofing Vulnerability
Exploitation Less Likely
No
4.6
CVE-2026-20931Windows Telephony Service Elevation of Privilege Vulnerability
Exploitation Unlikely
No
8.0
Microsoft Office vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-20946Microsoft Excel Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20955Microsoft Excel Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20956Microsoft Excel Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20950Microsoft Excel Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20957Microsoft Excel Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20949Microsoft Excel Security Feature Bypass Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20943Microsoft Office Click-To-Run Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20953Microsoft Office Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.4
CVE-2026-20952Microsoft Office Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.4
CVE-2026-20958Microsoft SharePoint Information Disclosure Vulnerability
Exploitation Less Likely
No
5.4
CVE-2026-20963Microsoft SharePoint Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.8
CVE-2026-20951Microsoft SharePoint Server Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20947Microsoft SharePoint Server Remote Code Execution Vulnerability
Exploitation Unlikely
No
8.8
CVE-2026-20959Microsoft SharePoint Server Spoofing Vulnerability
Exploitation Less Likely
No
4.6
CVE-2026-20944Microsoft Word Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.4
CVE-2026-20948Microsoft Word Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
SQL Server vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-20803Microsoft SQL Server Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.2
Windows vulnerabilities
CVE
Title
Exploitation status
Publicly disclosed?
CVSS v3 base score
CVE-2026-20815Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20830Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.0
CVE-2026-21221Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.0
CVE-2026-20835Capability Access Management Service (camsvc) Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20851Capability Access Management Service (camsvc) Information Disclosure Vulnerability
Exploitation Less Likely
No
6.2
CVE-2026-20805Desktop Window Manager Information Disclosure Vulnerability
Exploitation Detected
No
5.5
CVE-2026-20871Desktop Windows Manager Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20814DirectX Graphics Kernel Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20836DirectX Graphics Kernel Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20962Dynamic Root of Trust for Measurement (DRTM) Information Disclosure Vulnerability
Exploitation Less Likely
No
4.4
CVE-2026-20941Host Process for Windows Tasks Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20812LDAP Tampering Vulnerability
Exploitation Less Likely
No
6.5
CVE-2026-20842Microsoft DWM Core Library Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20847Microsoft Windows File Explorer Spoofing Vulnerability
Exploitation Unlikely
No
6.5
CVE-2023-31096MITRE: CVE-2023-31096 Windows Agere Soft Modem Driver Elevation of Privilege Vulnerability
Exploitation More Likely
Yes
7.8
CVE-2026-20925NTLM Hash Disclosure Spoofing Vulnerability
Exploitation Less Likely
No
6.5
CVE-2026-20872NTLM Hash Disclosure Spoofing Vulnerability
Exploitation Less Likely
No
6.5
CVE-2026-20821Remote Procedure Call Information Disclosure Vulnerability
Exploitation Unlikely
No
6.2
CVE-2026-21265Secure Boot Certificate Expiration Security Feature Bypass Vulnerability
Exploitation Less Likely
Yes
6.4
CVE-2026-20826Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20827Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20829TPM Trustlet Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20811Win32k Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20920Win32k Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20863Win32k Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20810Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20831Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20860Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20839Windows Client-Side Caching (CSC) Service Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20844Windows Clipboard Server Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.4
CVE-2026-20857Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20940Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20820Windows Common Log File System Driver Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20864Windows Connected Devices Platform Service Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-0386Windows Deployment Services Remote Code Execution Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20817Windows Error Reporting Service Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20808Windows File Explorer Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20823Windows File Explorer Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20932Windows File Explorer Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20937Windows File Explorer Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20939Windows File Explorer Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20822Windows Graphics Component Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20804Windows Hello Tampering Vulnerability
Exploitation Unlikely
No
7.7
CVE-2026-20852Windows Hello Tampering Vulnerability
Exploitation Less Likely
No
7.7
CVE-2026-20929Windows HTTP.sys Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20825Windows Hyper-V Information Disclosure Vulnerability
Exploitation Less Likely
No
4.4
CVE-2026-20816Windows Installer Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20849Windows Kerberos Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20833Windows Kerberos Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20818Windows Kernel Information Disclosure Vulnerability
Exploitation Unlikely
No
6.2
CVE-2026-20838Windows Kernel Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20809Windows Kernel Memory Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20859Windows Kernel-Mode Driver Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20875Windows Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability
Exploitation Less Likely
No
7.5
CVE-2026-20854Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.5
CVE-2026-20869Windows Local Session Manager (LSM) Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.0
CVE-2026-20858Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20865Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20877Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20918Windows Management Services Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20923Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20924Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20861Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20866Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20867Windows Management Services Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20873Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20874Windows Management Services Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20862Windows Management Services Information Disclosure Vulnerability
Exploitation Unlikely
No
5.5
CVE-2026-20837Windows Media Remote Code Execution Vulnerability
Exploitation Less Likely
No
7.8
CVE-2024-55414Windows Motorola Soft Modem Driver Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.8
CVE-2026-20936Windows NDIS Information Disclosure Vulnerability
Exploitation Unlikely
No
4.3
CVE-2026-20840Windows NTFS Remote Code Execution Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20922Windows NTFS Remote Code Execution Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20824Windows Remote Assistance Security Feature Bypass Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20832Windows Remote Procedure Call Interface Definition Language (IDL) Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20828Windows rndismp6.sys Information Disclosure Vulnerability
Exploitation Less Likely
No
4.6
CVE-2026-20843Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability
Exploitation More Likely
No
7.8
CVE-2026-20868Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.8
CVE-2026-20856Windows Server Update Service (WSUS) Remote Code Execution Vulnerability
Exploitation Less Likely
No
8.1
CVE-2026-20927Windows SMB Server Denial of Service Vulnerability
Exploitation Unlikely
No
5.3
CVE-2026-20919Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20921Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20926Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20934Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20848Windows SMB Server Elevation of Privilege Vulnerability
Exploitation Unlikely
No
7.5
CVE-2026-20834Windows Spoofing Vulnerability
Exploitation Less Likely
No
4.6
CVE-2026-20931Windows Telephony Service Elevation of Privilege Vulnerability
Exploitation Unlikely
No
8.0
CVE-2026-20876Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability
Exploitation Less Likely
No
6.7
CVE-2026-20938Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
CVE-2026-20819Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability
Exploitation Less Likely
No
5.5
CVE-2026-20935Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability
Exploitation Less Likely
No
6.2
CVE-2026-20853Windows WalletService Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.4
CVE-2026-20870Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability
Exploitation Less Likely
No
7.8
- Patch Tuesday
- Vulnerability Management